Table of Content
The concept of the Internet of Things (IoT) is slowly finding applicability across various industry verticals, resulting in a higher business value. IoT transforms process monitoring by connecting and tracking multiple devices within a network.
However, beyond the benefits of IoT lies a great challenge of ensuring security throughout the communication network. The threat is evident through the numerous incidents of illegal data manipulation and hacking devices on the network, such as cameras and vehicles.
IoT-connected gadgets have a bad reputation for poor security partly because they are often made cheaply and in haste and partly because they lack computing power. Conventionally speaking, it is not so easy to encrypt all that data with limited resources.
However, real-world data suggests that these tiny IoT gadgets and IoT sensors can run independent versions of traditional, time-tested encryption schemes. What is encryption, you ask? It is the process of encoding information or converting the original information into an alternative, also known as ciphertext. More on that in a bit.
An overview of IoT security in the business context
The biggest security-related threat of IoT systems is that even using devices for data collection from the real physical world can become a target of cybercrimes.
For example, deploying the IoT technology to a plant can significantly enhance productivity and maintainability via data collection from many sensors and modules installed in the production equipment.
Falsifying sensor data during the process can result in incorrect analysis and erroneous control. Even if there are no problems, it is important to consider risks and threats that might become evident or pronounced in the future.
Key definitions and concepts in the world of encryption
IoT is now subject to encryption regulations, and the technology must be applied to all devices within restricted environments. These regulations include various types of algorithms - simply known as IoT encryption algorithms.
These security tools protect IoT devices and networks from potential data breaches and communication vulnerabilities. So, how does encryption work? The original information, known as unencrypted data or plaintext, undergoes a simple process of translation known as encryption.
Under the process, the plaintext or original information translates into a secret code, which appears to be a useless set of random characters known as encrypted data or ciphertext. On the other hand, decryption translates the secret code to the original information through a process known as cryptanalysis.
The science of applying end-to-end encryption and decryption is known as cryptography, and the study of cryptography and cryptanalysis is known as cryptology. It includes various mathematical theories, formulas, and algorithms known as ciphers, also quoted as encryption or cryptographic algorithms.
Types of encryption in IoT
The ciphers use variables known as keys or cryptographic keys to lock and unlock encryption or decryption functions. Users create a secret security code known as the password to generate keys. These operate on two types of encryption:
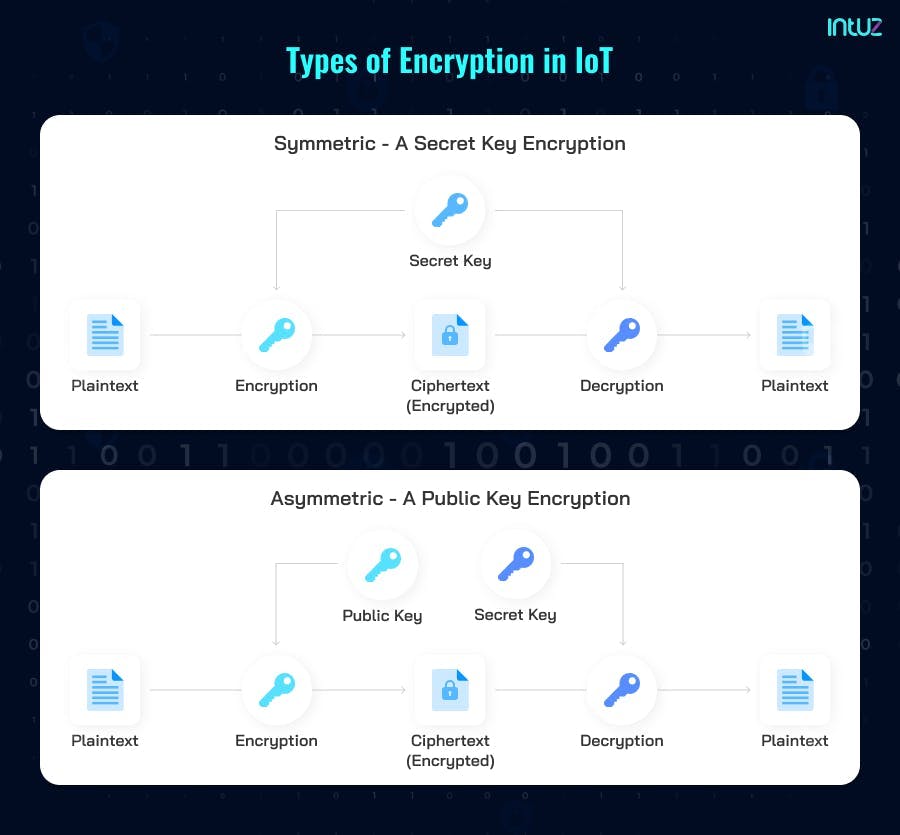
1. Symmetric - A secret key encryption
As the name defines, it uses the same single key to function encryption and decryption. In this case, it is a must that the sender and receiver agree on the shared secret key before establishing the secured communication.
Depending upon the data exchange requirement, symmetric encryption operates on stream (1 byte or 1 bit) and block ciphers (data of fixed size - usually 64 bits). It is faster, requires low power, and includes a simple, straight forward end-to-end process. AES, DES, IDEA, and Blowfish are examples.
2. Asymmetric - A public key encryption
Unlike Symmetric Encryption, it uses a key pair - a public key for encryption and a private key for decryption, linked mathematically and logically to each other.
Any sender can encrypt the data using the public key. However, the decryption is only possible by the intended recipient using the private key. Thus, asymmetric encryption involves authentication with strengthened security. The top examples are RSA, DSA, ECC, and TLS/SSL.
Since IoT architecture works on the heterogeneous distributed system, it uses the symmetric type for encryption and the asymmetric type for decryption to cope with the security challenges.
The best encryption algorithms for IoT
The fundamental security concerns of an IoT ecosystem are access control, privacy, and robust user authentication. The best encryption algorithms for IoT are:
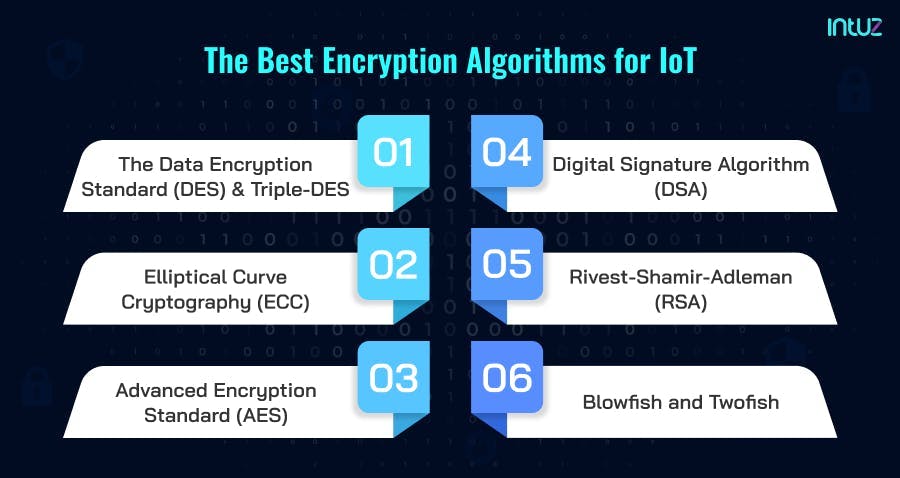
1. The Data Encryption Standard (DES) and Triple-DES
Both are the symmetric encryption algorithms wherein DES is the oldest and keystone of the cryptography, now phased out (due to low encryption key). Triple-DES is its successor, believed to be effective till 2030.
The Triple-DES overcomes all DES challenges, such as vulnerable meet-in-the-middle attacks, applies three 56-bit keys to every data block, and adds the total key length up to 168-bit.
However, there is the case of a mid-level vulnerability that depreciates its security level to a 112-bit key. Due to this, it is phasing out (replaced by AES). But some IoT products and financial services still utilize it because of its dependability, compatibility, and flexibility.
2. Elliptical Curve Cryptography (ECC)
It is an alternative to Rivest–Shamir–Adleman (RSA) and utilizes algebraic functions to create concrete security between “key pairs” (public and private keys).
Deploying the elliptic curve theory, ECC generates shorter, faster, and more efficient keys for encryption and decryption. That makes it the best fit for IoT devices, mobile applications, and those with limited computing (CPU) resources.
3. Advanced Encryption Standard (AES)
It is the most popular and robust symmetric encryption algorithm, which works on block ciphers from basic 128 to heavy-duty 192 and 256-bit keys. It is unbreakable (due to longer key length) and immune to cyber-attacks except for brute force.
As a result, the US gogovernment'sSA, NIST (developer of AES), and other large organizations extensively use AES to safeguard classified sensitive data. Also, it is the futuristic “best-fit standard application” for the private sector.
4. Digital Signature Algorithm (DSA)
Like RSA, it is also an asymmetrical encryption algorithm with a slight yet significant difference in the process. DSA uses an electronic/digital signature for data transmission, which makes encryption slower (as it involves authentication).
However, decryption is faster after the successful verification (through hash function). This operation uses the mathematical concept of modular exponentiation and the algebraic properties of the discrete logarithm.
Lightweight Digital Signature Based Security Algorithms are in research to establish secure communication in an IoT ecosystem.
5. Rivest–Shamir–Adleman (RSA)
It is a scalable asymmetrical encryption algorithm and is most trusted for the data in transit over the internet like SSL/TLS, S/MIME, SSH, cryptocurrencies, etc.
It efficiently defends against brute-force cryptographic hacks by using higher key lengths (768, 1024, 2048, 4096-bits, and more), which makes it difficult and time-consuming to decrypt the data. Hence, the go-to for IoT applications.
6. Blowfish and Twofish
Both are the leading license-free, public domain symmetric encryption algorithms wherein Twofish is the successor of Blowfish. Blowfish deciphers plain text into 64-bit data blocks and Twofish into 128-bits (in 16 rounds irrespective of key size). The high speed plus flexibility make them unbreakable and user-friendly.
Consequently, Blowfish is most suitable for securing e-commerce applications, online payments, and passwords. Twofish is an excellent choice for hardware and software solutions, extensively used for low processing resources.
Advantages of encryption in IoT
Businesses that have invested heavily in the traditional perimeter IT security firewalls and detection solutions want more vital data protection. From external hackers to internal staff, data protection for different formats and purposes is a humongous task. Encryption takes care of the following tasks:
1. It supports the set regulations and compliances under Payment Card Industry Data Security Standard (PCI DSS) and other market advanced encryption standards. That aims to protect the sensitive data of cardholders during online transactions.
2. It holistically safeguards confidentiality, authentication, integrity, and data privacy irrespective of location (cloud/local storage). It helps promote trust and enhances security at all times.
3. It is platform-independent and protects data at rest, in use and in motion, across various IoT devices, eventually strengthening the network communication.
Disadvantages of encryption in IoT
Amidst the rising IoT data security vulnerabilities, solid and undefeatable encryption is necessary. However, it comes with a few disadvantages:
1. The top problem is encryption key management at an enterprise level. Its maintenance is a colossal task, and if not deciphered with the corresponding private key, it does not give access to anyone. It may restrict access even for the data owners. The arrangement implies that all the associated data will get lost if you lose the encryption keys.
2. It includes considerably high expense in maintaining and upgrading the systems and backup servers that perform data security tasks. In addition, the recovery operation in a large-scale disaster consumes a lot of time.
3. The encryption backup and restoration process is complex and sometimes faces compatibility issues while integrating with IoT applications. This, in turn, adversely impacts the daily routine operations.
Therefore, data encryption needs a concrete strategy to backup the keys separately. It must be secure from cyber attackers and intruders but easily accessible for the data owners.
The application of cryptography in IoT
Conventional cryptography is unsuitable for IoT technology as it requires low-power computation resources. Although AES, SHA-256, and RSA/DSA/Elliptic Curve perform well together. However, they mostly struggle with IoT and embedded ecosystems.
That is why lightweight cryptography (LWC) is the best solution to deal with the next generation of IoT frameworks based on emerging 5G technology and Industry 4.0.
LWC is still at a nascent phase and has been found incredibly compelling for the small size, low-energy IoT products such as RFID tags, sensor networks, microcontrollers, contactless smart cards, smart watches, and so on.
PRESENT, CLEFIA, PICCOLO, PRINCE, and LBLOCK are the prominent lightweight cryptographic algorithms currently used in IoT applications in a testing environment.
Cyber experts are constantly optimizing the existing cryptographic standards and devising new algorithms to secure data transportation and communication channels.
Errors in data encryption
Errors in data encryption cost businesses a lot. Major data breaches lead to huge losses in brand reputation and monetary solutions. These errors originate due to sheer negligence and lack of knowledge. According to the World Economic Forum,” 5% of cybersecurity infringements arise because of human errors. It is an enormous figure, and large-scale enterprises cannot afford to ignore it. There are fundamentally two broad categories of human errors:
1. Skill-based errors due to slips and lapses occur because of fatigue or negligence while performing daily routine operations.
2. Decision-based errors occur due to the wrong choices due to a lack of knowledge.
The top six examples of human errors in end-to-end encryption are as follows:
Using poor and weak passwords
Getting trapped in phishing and social engineering
Mishandling high privilege sensitive data or accounts
Using outdated or unauthorized software in the official system
Using third-party platforms to share confidential corporate data
Misdelivery, especially in the case of email or online workspace communications
How To Protect Your Data Privacy In The Cloud?
Learn MoreAll of the above are resolvable with the below-mentioned six precautionary solutions
Incorporate corporate security policy and organize regular cybersecurity training
Perform regular IT audits
Enforce Zero Trust Security Policy with the least privileges
Opt for cloud storage management for easy data retrieval and restoration
Enable two-factor authentication to strengthen sensitive data/admin security
Block all third-party tools, USB devices, and applications to prevent cyberattacks
The future of IoT security
The expansion of IoT technology across industries has boosted the growth of a 360-degree security market. Though it has slow adoption, potential growth is evident thanks to the ongoing rapid technological developments, such as smart homes, 5G, and automotive.
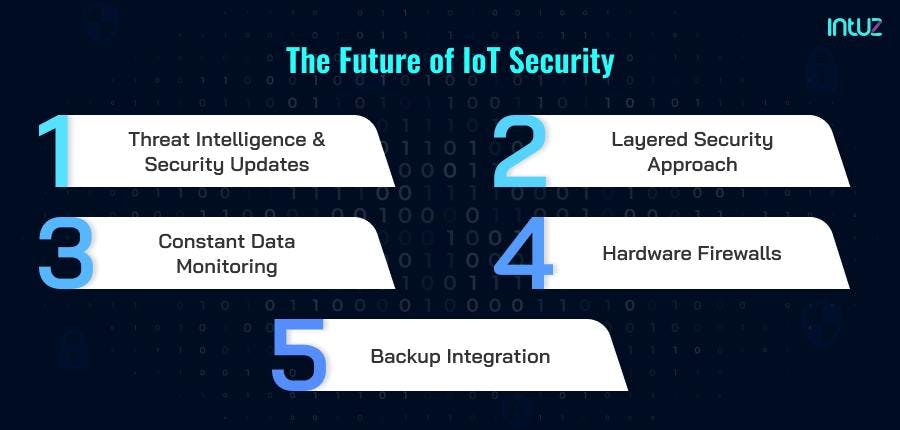
We will not be surprised to see IoT attracting full-stack protection services in the upcoming years. The future of IoT security is likely to be dependent on the below practices:
1. Threat intelligence and security updates
By 2025, the number of IoT connections per minute will be 1,52,200, producing approximately 73.1ZB of data. With such enormous data transmission, IoT devices should regularly receive security patches, including threat intelligence, to combat infringement risks.
2. Layered security approach
Since the IoT ecosystem is a network of heterogeneous devices, deploying multiple security layers at each data exchange point will be necessary.
3. Constant data monitoring
Amidst the 24*7 data exchange, IoT will help discover, monitor, manage, and analyze the overall dynamic systems, including billions of events and alerts. IoT monitoring will significantly defend the “inter and intra”-connected applications, including GPS signals.
4. Hardware firewalls
The IoT firewalls that are device and application-centric are known as hardware firewalls. Their core operation is to ensure protection from phishing scams, unauthorized remote access, and suspicious network traffic.
5. Backup integration
Cloud backup integration solutions will be the most suitable to handle and secure the edge computational-based IoT framework, including devices, networks, and data. Furthermore, network segmentation would be an added advantage to stop the attack's spread and isolate the infected machines.
Consumers also have a role to play in IoT security.
How can end-users find secure IoT devices? No one has to be an expert in data encryption to secure their internet-connected devices appropriately. IoT home and business security start with the network router.
Similarly, any new IoT device introduced to the system will have security settings by default, including resetting any default passwords for gaining network access and two-factor authentication (2FA) to keep software patches up to date.
The consumer IoT market is growing exponentially year over year and is predicted to reach $142 billion at a CAGR of 17.52% by 2026. Therefore, with the increasing popularity of this next-generation technology, it is equally important to educate consumers about the five IoT security essentials:
Changing the universal default password
Enabling two-factor authorization or 2FA
Updating the IoT devices with the latest software version
Communicating on an end-to-end secure network like password-protected Wi-Fi
Securing the personal data in a separate cloud-based storage system
IoT is already revolutionizing both the lifestyle and professional aspects of consumers. The scope of IoT is ubiquitous, from home automation to wearable technologies and industrial applications. Undoubtedly, it is making life much easier.
However, the increasing security challenges need special attention to prevent cybersecurity breaches on a disastrous level. Hence, in support of the existing Blockchain encryption algorithms, it is time to devise new defense mechanisms and standardize proposed lightweight cryptographic options to keep pace with the progressing IoT applications.
Over to you
The way IoT has transformed our lives - at both consumer and industrial levels - is fascinating! The technology has spread from home smart fridges to factory production line tracking. Therefore, the devices that connect to the internet must be encrypted because of the nature of data transmitted.
IoT users and security managers can minimize data breaches to a great extent and ensure a seamless experience through encrypted IoT networks and devices. If you want to know more about building secure IoT products for your business, contact us with your IoT app development project details.





