Table of Content
Unless you have been living under a rock, you will know that IoT is a convergence of embedded systems, control solutions, wireless sensor networks, and automation. From next-gen healthcare and smart retail to wearable devices and intelligent product enhancements - IoT has spread its wings across industries, and for a good reason.
From a business point of view, IoT technologies transform organizations with data-driven insights, enhanced operational processes, and more efficient use of resources and workforce. No wonder the IoT industry's size continues to grow exponentially and has acquired 12.2 billion active endpoints in 2021 alone.
Powered by AI, 5G, and Edge Computing technologies, the IoT landscape is estimated to grow at a CAGR of 18%, reaching 14.4 billion active connections by 2025. According to Deloitte, IoT is expected to have the most profound impact on organizations compared to other Industry 4.0 technologies such as Big Data, 3D printing, Blockchain, Advanced Robotics, and so on.
However, the fast-paced transition toward IoT has given rise to security concerns and a global impact on critical operations. As a result, there is a demand for concrete, uniform, and refined IoT protocols to cope with the futuristic communication challenges.
This article is written to help you understand the standard IoT protocols and power and connectivity requirements. But first, let us sort out the basics:
IoT protocols by definition and vision
IoT protocols aim to connect devices to IoT devices over a seamless and secure connection. The IoT protocols operate on four pillars - device, connectivity, data, and analytics. Their defense-in-depth security strategy shields the data transmission layer by layer.
While the business layer includes the management of billing and data marketplaces, the people who interact with IoT devices and technologies fall under the technology users layer.
The device layer comprises a combination of sensors, hardware, actuators, software, and gateways, constituting a device that connects and interacts with a network. The data layer involves the data collected, processed, stored, and analyzed in business contexts.
Optimize Your IoT Network: Let's Implement Seamless Communication Protocols!
Let's Get StartedWhy is IoT protocol important?
IoT protocols are an integral part of the IoT ecosystem. They are a set of defined rules and standards that ensure seamless communication between different devices in the IoT. The protocols are the foundation of data transmission, so condensing them for IoT impede is essential. These protocols are necessary for the IoT applications to communicate with each other seamlessly.
Data communication occurs through IoT protocols that ensure data is sent from devices or sensors and received by another device or sensor in the connected ecosystem of IoT. The protocols are important for the existence of IoT.
IoT protocol connection models
There is no set pattern for data routing, and the communication is highly dependent on the network topology. However, the fundamental models are used either as standalone or in combinations for IoT deployments, including:
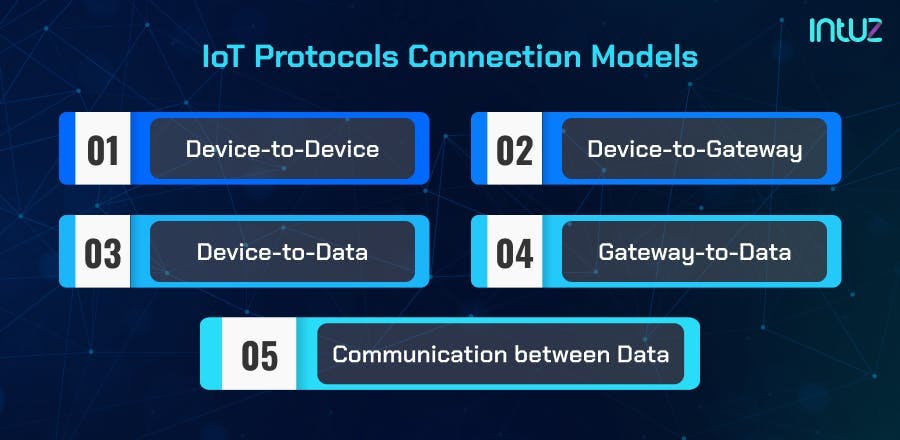
IoT protocols connection models
1. Device-to-device
It enables communication between nearby devices (proximity) using IoT Protocols like Bluetooth, ZigBee, Z-Wave, 4G, 5G, and WiFi.
2. Device-to-gateway
In this model, the devices communicate with the data system using a mediator platform, such as LPWAN, WiFi, and/or Ethernet IoT protocols.
The core functions of device-to-gateway are combining data from sensors, analyzing it, and routing it to the destination data system (data center or cloud). Also, in case of any problem, the connection model sends back the data to the source device.
3. Device-to-data
It works on edge computing, allowing devices to connect directly with the data source. A few popular device-to-data connection models include BLE, LoRaWAN, and Z-Wave.
4. Gateway-to-data
It is the simple communication between the mediator platform or central hubs and the data center or cloud. Open Automation Software (OAS) and Universal Data Connector are the best examples of robust IoT Gateways.
5. Communication between data
This protocol connection model allows data transmission between the data center and the cloud. It includes IoT Data protocols like MQTT, HTTP, REST, etc.
Types of IoT protocols
IoT protocols and standards are broadly classified into two separate categories, including IoT data protocols that have presentation or application layers and network protocols for IoT comprising datalink and physical layers:
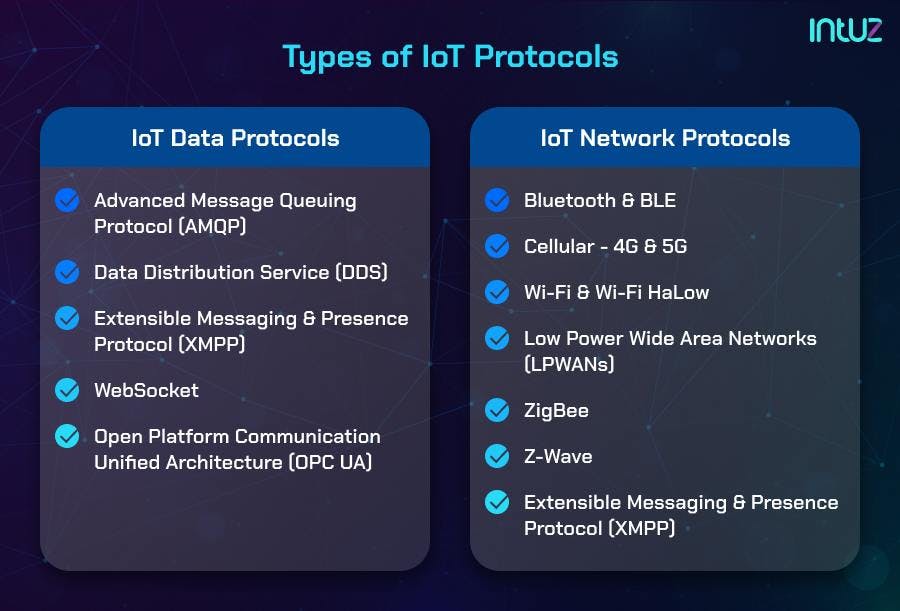
Types of Protocols
I. IoT Data Protocols
These protocols establish the end-to-end communication between low-power IoT devices and the hardware at the source, client, and/or user side, using only wired or cellular networks. The IoT data protocols function without an internet connection:
1. Advanced Message Queuing Protocol (AMQP)
AMQP is widely used in banking and finance as a message-oriented open standard software protocol. It comprises three crucial message components - Exchange, Queue, and Routing.
It is based on the Transmission Control Protocol and works on the architecture of "publish/subscribe" and "request/response" types. In addition, the guaranteed delivery or transaction message makes AMQP interoperable, secure, and reliable.
2. Data Distribution Service (DDS)
DDS is a UDP based "publish/subscribe" API that facilitates secure real-time M2M data sharing between the connected IoT devices. Furthermore, it works on broker-less scalable architecture (DCPS and DLRL), i.e., it operates independently of any hardware or software platform.
Its multi-purpose function simplifies IoT deployment for both small devices and high-performance networks.
3. Extensible Messaging and Presence Protocol (XMPP)
XMPP is a decentralized, open-source, and secure protocol developed using XML language to enable real-time data exchange. It operates as a presence indicator by reflecting the status of available servers and devices. XMPP-IoT is a lightweight version of XMPP and is the best for consumer-oriented IoT deployments as it is extensible, scalable, and flexible.
4. WebSocket
Introduced by HTML5, WebSocket is an event-triggered independent TCP-based IoT protocol or API. It establishes full-duplex real-time communication between the client and server.
Using advanced technology streamlines complexities involved in the bi-directional transmission over the internet. And, it is suitable to maintain constant connectivity across heterogeneous IoT devices. Notably, WebSocket is much faster than HTTP.
5. Open Platform Communications Unified Architecture (OPC UA)
OPC UA is a next-generation data model technology ideal for Industry 4.0 and IoT. It operates on a platform-independent, encrypted, and extensible multi-layered architecture. In addition, its service-oriented framework supports both "publish/subscribe" and "request/response" models.
As per the latest press release published by OPC Foundation, leading IoT vendors such as SIEMENS, SAP, Microsoft, IBM, AWS, and Google Cloud are already leveraging OPC UA for edge-to-cloud applications.
II. IoT Network Protocols
These protocols constitute specific standards, policies, and unified rules to establish secured communication between IoT devices over the internet.
With emerging advancements in the IoT ecosystem, these protocols utilize multiple technologies that work on network topologies. The most widely used are star and mesh topologies. Following are the extensively used IoT network protocols:
1. Bluetooth and BLE
Bluetooth is the top choice for shorter-range wireless communication, preferably for personal 2.4 GHz networks. Bluetooth Low Energy (BLE) is its optimized version and the standard protocol for IoT architecture.
The latest version of Bluetooth is 5.3. It was released on 13th July 2021 and is still in beta. Bluetooth best suits beacons, fitness, automotive, retail, and audio IoT applications.
2. Cellular - 4G and 5G
Cellular is a wireless mobile communication network technology that facilitates large bandwidth and reliable broadband services. Currently, 3G is almost on the verge of extinction. On the other hand, 4G is leading but not suited for IoT applications due to higher cost and power consumption. However, the new-age 5G is ideal for IoT applications across industries and personal usage.
3. Wi-Fi and Wi-Fi HaLow
WiFi is the most popular and conventional wireless network protocol for home and commercial usage. But, it is not very flexible and scalable for IoT purposes. WiFi HaLow (IEEE 802.11 ah) is a unique solution to overcome its challenges. This high-level communication protocol provides a long-range between 750 and 950 MHz with low-power connectivity.
4. Low Power Wide Area Networks (LPWANs)
LPWANs are a new set of wireless network protocols devised to set up communication between low-power IoT applications over long ranges. They are a cost-saving option because they operate on small and affordable batteries that are long-lasting and power-efficient.
MIOTY, LoRaWAN, 6LoWPAN, Thread, NB-IoT, LTE-M, SigFox, and HayStack are purpose-built LPWANs for large-scale IoT deployments.
5. ZigBee
ZigBee is a mesh wireless communication protocol that operates on a 2.4 GHz network. It is short-range, highly interoperable, low-power consuming, and facilitates massive data transfer in a single instance with high security. ZigBee is most appropriate for small, and medium ranged IoT devices such as microcontrollers, sensors, gateways, and so on.
Notably, due to its mesh grid structural design, the connectivity can be extended over a long distance using multi-hop routing. ZigBee is best suited for commercial building and innovative home automation applications. Actually, it is the safest wireless protocol for transferring real-time patient data from a sensor.
MQTT vs. AMQP: IoT Protocols You Must Know About
Learn More6. Z-Wave
Similar to ZigBee, the Z-Wave protocol also works on mesh network topology. However, it is most prominent for IoT home automation applications. Z-Wave is a Radio Frequency (RF) based, less power-consuming wireless communication technology that operates on 800-900 MHz and is purely location-dependent. As a result, it hardly faces any connectivity hindrance. It facilitates safe and steady data transmission with low latency.
7. Extensible Messaging and Presence Protocol (XMPP)
This technology dates back to the early 2000s and was designed for real-time human-to-human communication. XMPP is now used for M2M communication and for routing XML data.
XMPP supports the real-time exchange of structured but extensible data across multiple network entities, making it suitable for consumer-oriented IoT deployments, such as smart appliances and wearables.
Other than the above-stated options, the network protocols such as Lightweight M2M (LWM2M), Radio-frequency Identification (RFID), Near Field Communication (NFC), Ethernet, and Wi-Sun have contributed significantly towards setting up the sustainable connection in the IoT space.
Therefore, be it for home or commercial usage, the selection of an ideal IoT network protocol must consider the parameters of bandwidth, range, power consumption, latency, intermittent connectivity, Quality of Service (QoS), and security.
Benefits of IoT wireless protocols
IoT protocols form a crucial component of the IoT infrastructure. They serve higher data throughput with lesser complexities. Wireless IoT protocols have become the first choice solution for personal and industrial usage. The rising demand for wireless IoT protocols is because of the core benefits:
- Affordability
- Less time and energy consumption
- Robust security and data privacy
- Good network coverage and connectivity
- Automated and streamlined communications
- Faster data transfer and smoother operations
- Easy setup and deployment in the IoT infrastructure
- Simple to use while resulting in enhanced productivity
Market reports estimate the IoT market will potentially grow to 14.4 billion global connections this year, and WNAN, WLAN, and WPAN alone will hold an 11-24% CAGR for the 2021-25 session.
How to choose the right IoT protocols?
Step 1: Assess Application Requirements
To get started, the first step you need to consider is determining
- What type of IoT application do you want to build?
- What are the specific protocol requirements you need to consider?
While analyzing the protocol needs, ensure that various aspects such as power limitations, response time to data query, type of data, volume of data, and how much data is being transferred are assessed. Protocol requirements differ from case to case. IoT applications with low latency need different protocols than low-data with low-life senors.
Step 2: Prioritize Security Considerations
IoT technology deals with sensitive data so data security is the primary need. To establish strong security, you need to follow IoT protocols. Analyze and select protocols that support secure communication, authentication, and encryption.
For example, MQTT offers features like SSL/TSL to ensure improved security. Considering other protocols, you might add a layer of enhanced protection. Prioritize and choose the IoT protocols that meet your security needs and make your IoT ecosystem safe.
Step 3: Evaluate Network Architecture
IoT devices or sensors work in a network. This could be a cloud network, a local network, or an amalgamation of both. Thus, you can understand how your IoT devices are connected to a network. If you want to implement IoT protocols for a large-scale network where connection across multiple devices is required, you can consider protocols such as ZigBee or LoRaWAN.
While implementing IoT protocols in your IT infrastructure, you need to assess
- How easily can you integrate the IoT protocol into your existing IT infrastructure?
- How to choose the right set of protocols that offers outstanding scalability, seamless data transfer, and improved communication?
Step 4: Analyze Use Case Specifics
Every IoT protocol serves you in different ways. They provide optimum results when considered for specific use cases.
For example,
- If your IoT infrastructure works in a high-latency environment and has a low bandwidth, then go with MQLL.
- When you have to run IoT devices or sensors using limited resources and networks, CoAP will be an ideal choice for you.
So, you need to consider the IoT protocol based on your specific use cases. The most common use cases of IoT implementation are remote monitoring, smart cities, industrial automation, etc. Selecting the right protocols helps you boost solution performance.
Step 5: Compare Protocol Capabilities
Choosing the right protocols is difficult as different protocols have different capabilities. Some are good at optimizing data throughput and speed, while others are capable of providing higher power and range efficiency.
So, based on your requirements, you can select the right set of protocols. With the help of an expert, the selection and implementation of IoT protocols will be quite easy for you.
To make the correct choice you need to compare the features of varied protocols such as scalability, data transmission rate, bandwidth, power consumption, and more.
For example,
- If your IoT application needs less energy consumption and short-range communication, Bluetooth integration will be the best choice.
- For the low-range and low-power applications, you can implement NB-IoT.
Step 6: Test and Implement
Now that you have selected and implemented the right protocols into your IoT ecosystem, you should first go with pilot testing. Check the impact of protocols on the small subset of devices. Perform testing for scalability, latency, reliability, packet loss, etc. components.
Monitor the performance and results of protocol implementation in real-time situations. Check the impact of protocols before they are implemented in your IoT application on a larger scale to ensure its sustainability. Make the required adjustments if you find any improvement areas during testing. This ensures you guaranteed results.
IoT Protocol Layers
IoT works on various networking technologies based on the IT infrastructure requirements, and therefore, it needs architecture to establish a coherent IoT ecosystem.
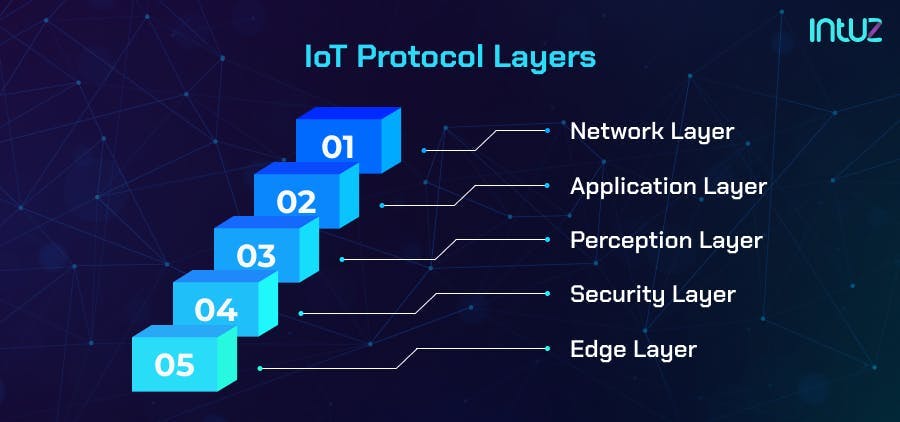
IoT Protocol Layers
Considering the complexities involved in the configuration, operations, functionalities, and communications, the five layers of IoT architecture are best suited for all purposes. Here is a look at how each layer helps in simplifying the structural design:
1. Network layer
Its core function is to connect the IoT devices with the network systems and servers. The network layer also helps to route and control the data transmission with the help of set communication protocols and unified formats.
Utilizing the TCP/IP stack and cellular and wireless technologies depending on the specification, the network layer helps set up secure transmission across all interconnected devices. A few examples are IPv4/IPv6, ICMP, IGMP, ARP, 3G/4G/5G, UDP, 6LoWPAN, and WiFi.
2. Application layer
It acts as an interface between the IoT devices and the end users or any other device that requests the information over the secured network. After successful data processing, formatting, and presentation, it produces the final information. A few examples of the application layer are HTTP, FTP, POP, IMAP, TLS, SMTP, DNS, TFTP, SNMP, and TELNET.
The IoT application protocol depends on four crucial parameters - latency, reliability, bandwidth, and transportation. Considering the same, along with the correspondence of the specifications and features, the following are the top five IoT application protocols:
- Representational State Transfer (REST)
- Constrained Application Protocol (CoAP)
- Advanced Message Queuing Protocol (AMQP)
- Message Queue Telemetry Transport (MQTT)
- Extensible Message and Presence Protocol (XMPP)
3. Perception layer
It constitutes sensors, actuators, and AI-powered devices to gather valuable details about the surrounding physical objects or the environment. The accumulated data is converted from analog signals to digital format for further operations.
Its functioning includes identification, information collection, and automated control technologies to channel the digital and real worlds. A few examples of the perception layer include surveillance cameras, bar codes, portable PCs, RFID, WSN, and GPS.
4. Security layer
It minimizes the risk of potential cyberattacks on the most vulnerable areas of the IoT ecosystem. The security checkpoints occur at three significant places - the device (including hardware and software), cloud, and connection.
With the rapid digital evolution during the outbreak, the security challenges and underlying threats to the IoT architecture also grew exponentially. Therefore, the layered security approach has become of utmost importance in the ongoing scenario.
A few examples of the security layer include Trusted Platform Module (TPM) chips, multiple authorizations, firewalls, NAC, AAA, NAP, IPS encryption, and cryptography mechanisms.
5. Edge layer
It works on the edge computing framework to improve latency, bandwidth, and real-time communication challenges. The edge layer's primary goal is to fetch and process the requested information closer to the data sources.
With the ever-increasing number of smart devices over a centralized cloud system, the 'delay in response' is a significant concern. However, combined with 5G and AI capabilities, edge IoT layers perform exceptionally well for time-sensitive data and deliver faster results.
A few examples of the edge layer include electronic vehicles, smartphones, smartwatches, laptops, security cameras, V2X, public transit applications, smart cities, and green technologies. The five layers of IoT architecture facilitate the smooth functioning of the IoT ecosystem.
Besides, they can accommodate expansions and handle intricacies following the latest technological advancements. The goal is to establish seamless IoT interoperability, taking care of the 3Cs - change, compatibility, and cybersecurity.
Ready to Make Your IoT Data Flow Effortlessly?
Let's Talk ProtocolsIoT protocols hold much importance in this day and age.
The IoT technology ecosystem supports dozens of IoT wireless protocols, compelling many experts to call for global protocol standardization. However, given the fragmented nature of the ecosystem, the IoT market will probably never need an all-embracing standard.
Again - it should be noted that safe and effective device management is the keystone to the sustainable development and management of IoT networks worldwide.
The communication, data sharing, and usage of information by intelligent devices happen in a full-stack IoT ecosystem. A unified global protocol standardization thus becomes crucial to eliminate IoT fragmentation and potential security threats.
IoT protocols are the medium of communication or a shared language that helps establish connections between different smart devices and helps them interact with each other. They are essential for holistic device management.
IoT protocols consider the needs, communication, and security of the various devices integrated. Depending upon the IoT architecture, present scenario, and usage context, different IoT protocols are designed to minimize the risk of intrusion.
If you are looking for an IoT expert who knows how to optimize your operational core to build IoT-connected systems for you — regardless of sector - you have come to the right place.
We have worked on numerous IoT projects since our conception, and we would be happy to help you with your requirements.
Book a Free 45-minute Consultation with Our IoT Experts Today! Get a customized roadmap and strategies to leverage IoT to streamline data communication with protocol integration.






