Table Of Content
Companies in IoT have many things to factor in, including cost, convenience, and feasibility. But one thing that stands out is data protection and asset management. Safeguarding user privacy has become more critical than ever. That is where identity and access management (IAM) comes in handy, for they help companies put specific processes in place that help them stay away from cyberattacks and data leaks in the long run. Let us study the concept in detail:
The world of the Internet of Things (IoT) is expanding at a rapid pace. Connected devices continue to streamline business processes and make lives easier for general consumers, thus adding extravagant revenue streams for companies dealing in IoT.
This is not surprising given how it is now possible to develop enhanced experiences for consumers across industries by creating a strong and trusted relationship between devices, sensors, servers, and, of course, data.
Companies in the IoT landscape have a significant challenge in front of their eyes: time, cost, and convenience. But what is more of a concern is ensuring data security and privacy for consumers. Yes, that is right.
Data leaks in the IoT space
Safeguarding user privacy is becoming increasingly difficult as the IoT gains precedence in our day-to-day lives. More devices are connected than ever before, which means less control over increased data collection and connectivity activities.
In fact, control can be lost if someone hacks into the computer or smartphone, acting as a remote for other devices. This form of cybercrime can go undetected for a very long time unless a significant string of events takes place and shakes up the user.
Plus, smartphones especially store a humongous amount of personal data about their owners. There are apps linked to email IDs, bank accounts, and in some cases, household appliances and vehicles. Stolen data can result in massive (and in many cases, unsolvable) problems.
Consumers want control over their data.
Regardless of the IoT app, no consumer wants to lose control of their data. They want to determine what and who gets access to their personal information, for how long, and under what circumstances.
That is a challenge that will only increase with time as our world contracts and becomes more connected. This includes the individuals or businesses accessing the IoT services and the operators and enterprises authenticating and authorizing those services.
In the age of IoT, the issue is not that the connected things cannot be accessed properly. But instead, access to devices increases the risks of data leakage and, thus, must be protected.
Safeguard Your IoT Data: Schedule an IAM Strategy Session!
Schedule NowIAM and IoT: Managing access efficiently
IAM, short for Identify Access Management, is a body of technologies and policies to ensure that the right users have the appropriate access to technology resources. IAM also helps identify devices, besides managing user access to data.
An IAM solution should be efficient, productive, and secure, and work in sync with today's mobile and digital workforce with ease. As discussed previously, defining and managing device identity in the IoT ecosystem is a top priority for companies.
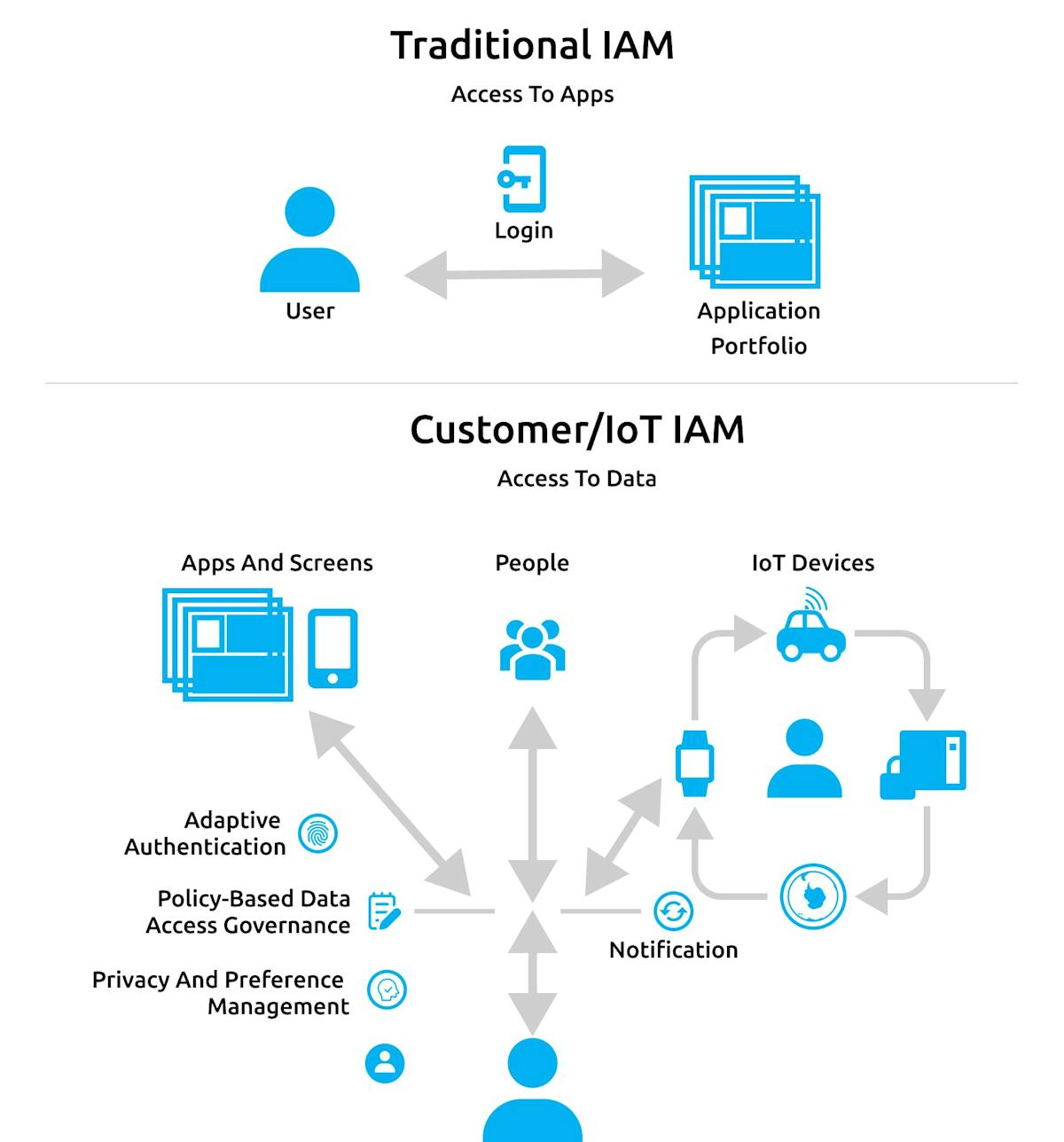
As traditional IAM solutions cannot deal with the new-age demands of IoT devices, there is a need to upgrade the architecture pronto, keeping in mind the number of device connections and the looming security concerns.
Market trends in IAM for IoT
The demand for IAM gained precedence only a couple of years ago when it became evident that IoT technology was not going anywhere. Quite interestingly, three market forces have converged into drive identity, access and connection in the IoT landscape, namely:
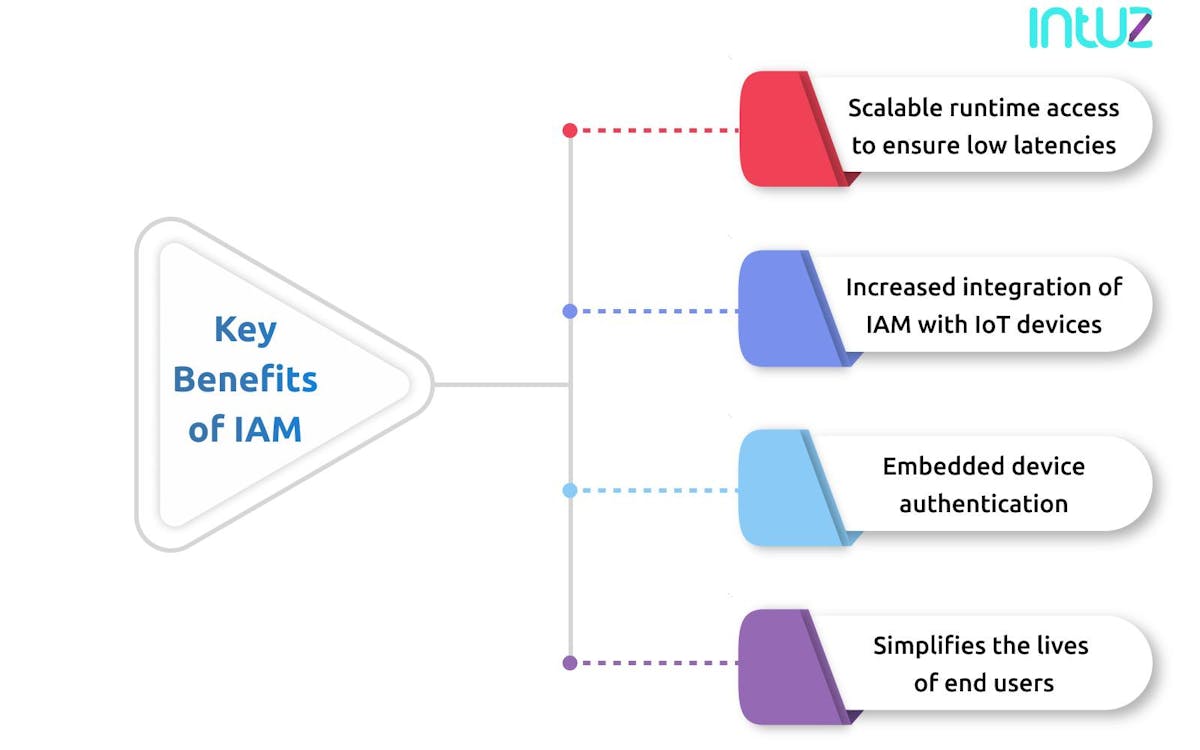
1. Scalable runtime access to ensure low latencies
Given the pace at which new IoT devices are entering the market, IoT vendors must provide scalable runtime access for securing authentication and authorization at high transaction rates — without facing high latencies.
Moving forward, the vendors must reduce data storage footprint and manage both structured and unstructured data sets to improve support for deployment on-premise and on the cloud platforms.
When the foundation has been smoothed out, it will be easier to transmit data between devices without worrying about latencies. Is it not the whole point of IoT platforms?
2. Increased integration of IAM with IoT devices
IoT platform vendors generally lack the concept of managing user identities. However, now the trend is changing as many have started incorporating various device identity and access technologies with IoT platforms for simplistic security designs during the IoT app development process This further speeds up the adoption of IAM in many IoT market segments. In fact, this is what is required to ensure that user data remains protected at all costs.
3. Embedded device authentication is important
Most IoT device manufacturers are not well-equipped to serve the authentication requirements, including design and security controls and device firmware.
Given the niche IoT products coming up in the market, it is evident that such manufacturers are now joining hands with niche authentication providers and product specialists to create an authentication process that is dynamic and robust.
There is, of course, a long way to go for the industry-specific authentication standards to solidify and find acceptability in the market. However, the emphasis on promoting industry-specific standards is more potent than ever.
IoT IAM roles: An overview
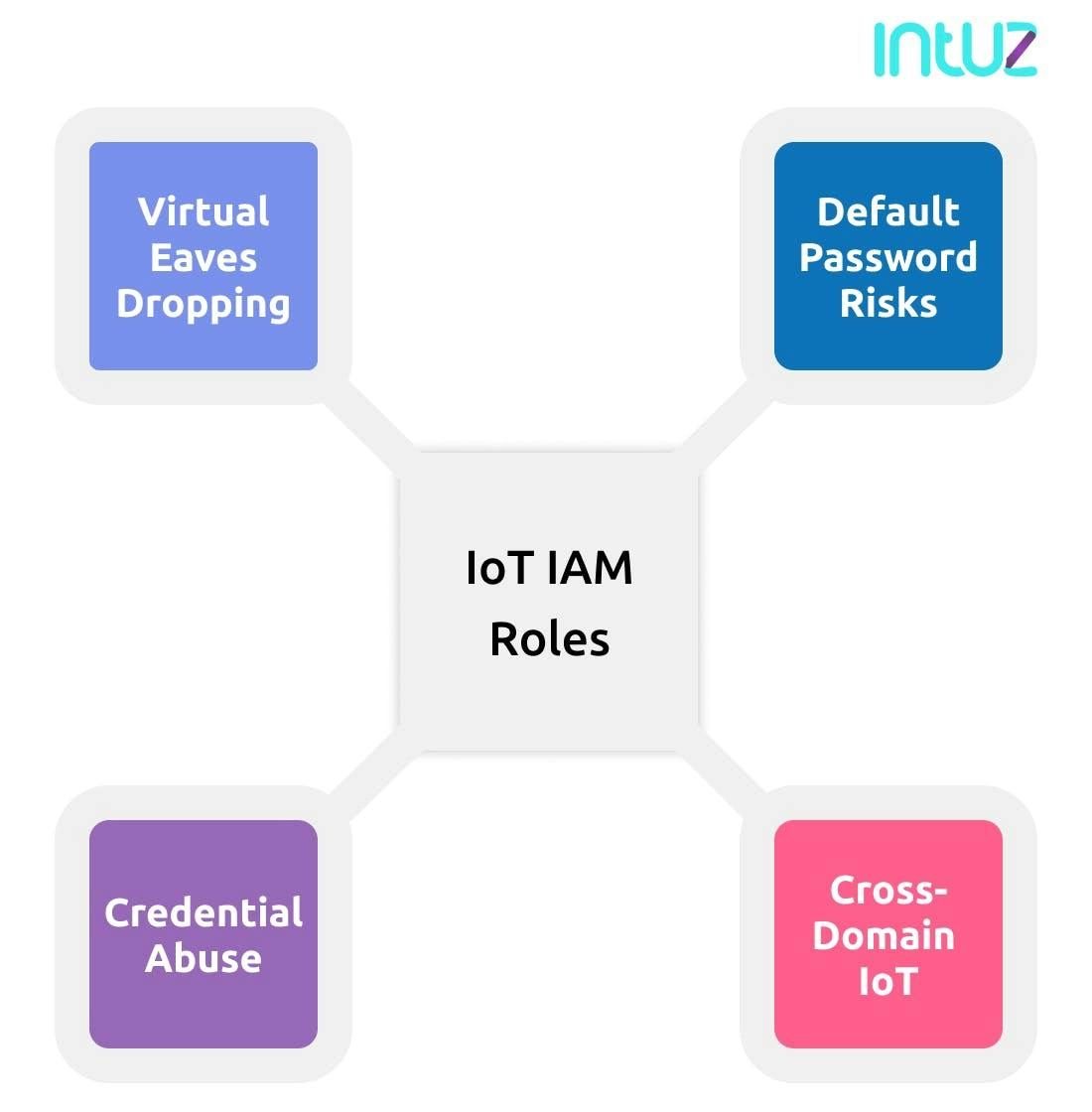
Without further ado, let us look at four ways in which identity and access management play a huge role in IoT app development services:
1. Default password risks
Many IoT devices come with default passwords. Meaning, customers are then instructed to change them later on. However, not everyone remembers to do so or bothers to act responsibly. Besides, those who change the password use common username/password pairs.
That does not serve the purpose of using the IoT device on a secure line. Ever since California legislators passed the California Consumer Privacy Act (CCPA), the connected IoT apps must encrypt unique passwords for those manufactured and sold. However, there is a flip side.
If everyone in the business knows the passport, then even those with limited privileges will access the device. But this can be fixed with added plugins and workflows.
2. Cross-domain IoT
The rapid expansion of the IoT ecosystem calls for a clearer understanding of how digital identities work today. Since IoT comprises several domains, it is necessary to manage the single and/or overlapping identities stemming from them.
A cross-domain IAM solution can help the business manage multiple identities across devices and domains perfectly. This will help them operate successfully in their environment.
3. Credential abuse
It means using stolen credentials like usernames and passwords to access sensitive data deliberately in layman's terms. It is a criminal offence, and that is also a common one. In workplaces especially, this can happen
when employees innocently or unknowingly share their passwords with coworkers.
They may do this to help their colleagues because they do not want to hamper the workflow or miss a deadline. But if they forget to renew their passwords, that can be a problem. Unfortunately, in many cases, it is the unlawful intent driving credential abuse.
The lack of a proper IAM solution makes it very easy for hackers to have high-level access to places or data they can easily exploit. This, however, can be resolved and controlled to a great extent. With an IAM platform, you can control all your interlinked devices and make them strong enough to shield data at a corporate level.
4. Virtual eavesdropping
Many IoT devices are linked to virtual personal assistants like Alexa or Siri — but a more advanced version. Their job is to listen to you and collect information. However, not many businesses are clear about how they plan to use the data collected through VAs.
There is always a reason to worry that the personal assistants might spill the company secrets or leak sensitive information, which would affect the brand reputation in the market.
Therefore, to address these challenges, businesses must design a purpose-built solution, which would conveniently include:
- Superlatively equipped preference and consent management system for users to control their IoT ecosystem.
- Responsive authentication and data access protocols for contextual control.
- End-to-end encryption for data protection at endpoints — between two different devices — and everywhere else in between.
At the end of the day, covering all bases for 360-degree user security is in the hands of businesses. And the sooner they deploy technology that helps them gain control, the better it is. No one wants a lawsuit or a terrible cyber attack on their hands.
Identifying users and "things" for better security
In this day and age, digital mobile solutions are critical for further amplifying revenue streams — regardless of your target audience (B2B/B2C), the industry niche, and business size. However, this also brings forth the terrifying issue of identity exposure and unnecessary cyber threats.
When it comes to custom IoT services, you have to take care of content, identity validation, trust management and attribute sharing. Some IoT devices may need more security than others, so you must deploy stringent protocols to safeguard user identity.
For instance, banking apps have the highest multi-factor authentication (MFA), authorization and consent. Given the typical lifespan of an IoT device, having suitable algorithms must ensure smooth authorization and encryption activities.
Managing access using policies made easy.
A single IAM system can be used to build, modify, and delete users. It can also be integrated with one or more directories and sync with them. IAM platforms can create different user identities that would need a particular type of access for the business.
That means the users can use a tool they are allowed to, thus protecting sensitive information and keeping user details safe. In addition, users can be segmented into roles and given access based on the role hierarchy.
When you know who controls what, you are better prepared to keep your information safe and have a solid handle on user management. Without IAM, this becomes too tedious to handle in the long run as your business grows.
Different types of identity-based policies
For starters, you can provision or de-provision users to use the IoT device. For instance, you can specify which tools and access levels (viewer, administrator, editor) are granted to an individual group or person. This is called provisioning.
Since the IT departments manage the IAM tools, they can undertake this task efficiently. Moreover, they can provide users based on the policies defined for role-based access or RBAC. It is very time-consuming to specify every employee's access to every asset of the business.
Taking away that control is called de-provisioning, which usually happens when a person leaves a particular team or company. This is to avoid security risks presented by ex-employees who have access to sensitive company information.
IAM systems authenticate users by confirming that they are who they say they are, thanks to multi-factor and adaptive authentication.
The future of IAM is now.
Traditionally speaking, employee-based and customer-based IAM platforms were restricted to devices such as computers and smartphones. However, the concept has drastically evolved to be included in every device humans use — from desktops to wearables.
When integrating IoT devices with your access management tools, you should consider:
- Establishing company procedures for access control
- Determining the process for registering IoT platforms
- Creating a flexible and agile lifecycle for your IoT technology
- Deciding authentication and authorization processes for Identifying and deploying security protocols that protect personally identifiable information (PII)
IAM is going to scale up and transform into an essential aspect of the IoT landscape. The IAM solutions should be efficient, secure, productive, and compliant. Companies are now searching for IAM solutions that work well with a mobile or remote workforce (given how the pandemic has changed the way we traditionally worked).
Maximize IoT Efficiency and Security with Custom IAM Solutions!
Let's Get StartedWrapping Up
This also calls for businesses to create policies that are based on contextual information. You must find an IoT app development company like Intuz that can help you deliver quick access permission to employees, vendors, and other stakeholders.
Book a Free 45-minute Consultation with Our IoT Experts Today! Get a customized roadmap and strategies to leverage IAM solutions that are flexible, scalable, and governable.






